In an IBM/HCL Workload Automation (WA) deployment, communication between the MDM (Master Domain Manager) ó DWC (Dynamic Workload Console) and MDM ó DA (Dynamic Agent) is implemented using SSL protocol, TLS v1.2 over TCP/IP. WA provides Self-Signed certificates (signed by IBM) with the product and all components use them by default to establish SSL communication. To enhance security, these certificates must be replaced with commercial CA (Certificate Authority) signed certificate for each server in the environment.
The following sections describe the procedure to replace various certificates.
1.1 Overview of SSL in WA
WA utilizes IBM WebSphere Application Server Liberty Profile (WLP) as the frontend web user interface as well as the backend engine. As such, there are two WLP that provide the services for DWC and MDM. The SSL implementation in WLP for DWC and MDM requires two stores to be present.
KeyStore Is a file to store private keys in the form of Personal Certificates.
Some KeyStores also contain trusted or public keys.
TrustStore Is a file to store public keys in the form of Signer Certificates.
Some TrustStores also contain trusted or private keys.
Personal Certificate Represents the identity of a server and contains a private key for signing/encrypting data.
Signer Certificate Represents the identity of a server and contains a public key
for decrypting data.
Certificate Chain Is a concatenation of CA signed server certificate and certificates of Intermediate and Root CAs.
Trusted CAs Is a concatenation of trusted CA certificates.
SSL Certificates are imported into the KeyStores for each profile and then the public keys are extracted and imported into the TrustStores.
The stores can have different formats for compatibility and security reasons and used by different components as shown below.
JKS Java Key Store
Used by the MDM and DWC WLP as well as a component of the Dynamic Agent
File extension is jks
CMS Cryptographic Message Syntax
Used by the Dynamic Agents
File extension is kdb
There are different types of file extensions used to signify the type of certificate or key it contains as described below.
CSR A Personal Certificate Signing Request contains the request to be sent to the CA for signing. It is generated from a KeyStore.
CRT A Personal Certificate that is signed by the CA. It is imported into the KeyStore
CER A Personal Certificate that is signed by the CA or a public key for root CA,
Intermediate CA, server exported from a KeyStore and imported into a TrustStore
KEY A label for a signed certificate after imported into a KeyStore
ARM A Signer Certificate chain. It is exported from a KeyStore and imported in to a
TrustStore.
PEM Privacy-Enhanced Mail is an encryption format used by the CAs.
1.2 Replacing Certificates used by MDM and DWC
The MDM and DWC each have one KeyStore and one TrustStore in JKS format. They are located in the following directories:
MDM /opt/IBM/IWA/IWS/usr/servers/engineServer/resources/security
KeyStore TWSServerKeyFile.jks
TrustStore TWSServerTrustFile.jks
DWC /opt/IBM/IWA/DWC/usr/servers/dwcServer/resources/security
KeyStore TWSServerKeyFile.jks
TrustStore TWSServerTrustFile.jks
TWSServerKeyStore.jks
This KeyStore contains the private and public certificates for the server, the Root and Intermediate public certificates of the CA that signed the server certificate. The public certificate of the server is exported and imported into the TWSServerTrustStore.jks and TWSClientKeyStore.
TWSServerTrustStore.jks
This TrustStore contains the public certificates for the server, the Root and Intermediate public certificates of the CA that signed the server certificate.
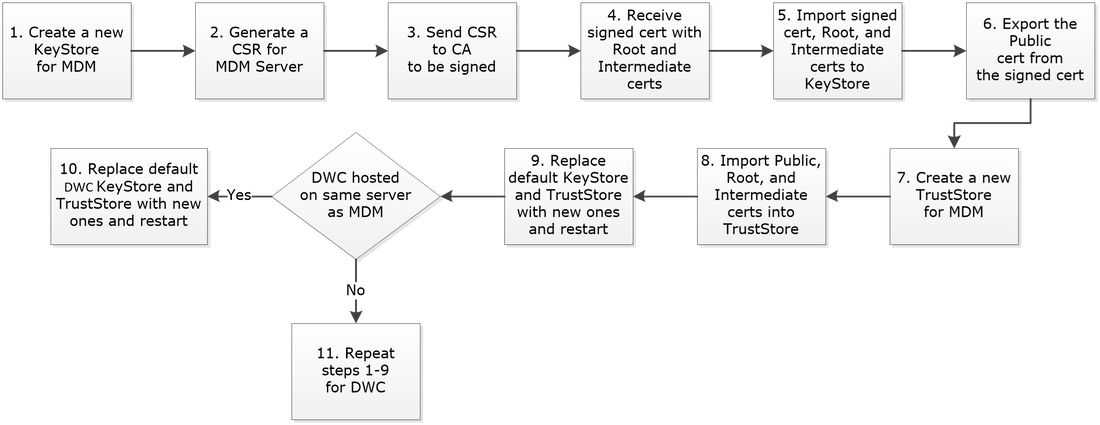
The following is a high-level procedure to replace the default certificates used by MDM and DWC.
The flow chart below depicts the procedure.
1.1 Overview of SSL in WA
WA utilizes IBM WebSphere Application Server Liberty Profile (WLP) as the frontend web user interface as well as the backend engine. As such, there are two WLP that provide the services for DWC and MDM. The SSL implementation in WLP for DWC and MDM requires two stores to be present.
KeyStore Is a file to store private keys in the form of Personal Certificates.
Some KeyStores also contain trusted or public keys.
TrustStore Is a file to store public keys in the form of Signer Certificates.
Some TrustStores also contain trusted or private keys.
Personal Certificate Represents the identity of a server and contains a private key for signing/encrypting data.
Signer Certificate Represents the identity of a server and contains a public key
for decrypting data.
Certificate Chain Is a concatenation of CA signed server certificate and certificates of Intermediate and Root CAs.
Trusted CAs Is a concatenation of trusted CA certificates.
SSL Certificates are imported into the KeyStores for each profile and then the public keys are extracted and imported into the TrustStores.
The stores can have different formats for compatibility and security reasons and used by different components as shown below.
JKS Java Key Store
Used by the MDM and DWC WLP as well as a component of the Dynamic Agent
File extension is jks
CMS Cryptographic Message Syntax
Used by the Dynamic Agents
File extension is kdb
There are different types of file extensions used to signify the type of certificate or key it contains as described below.
CSR A Personal Certificate Signing Request contains the request to be sent to the CA for signing. It is generated from a KeyStore.
CRT A Personal Certificate that is signed by the CA. It is imported into the KeyStore
CER A Personal Certificate that is signed by the CA or a public key for root CA,
Intermediate CA, server exported from a KeyStore and imported into a TrustStore
KEY A label for a signed certificate after imported into a KeyStore
ARM A Signer Certificate chain. It is exported from a KeyStore and imported in to a
TrustStore.
PEM Privacy-Enhanced Mail is an encryption format used by the CAs.
1.2 Replacing Certificates used by MDM and DWC
The MDM and DWC each have one KeyStore and one TrustStore in JKS format. They are located in the following directories:
MDM /opt/IBM/IWA/IWS/usr/servers/engineServer/resources/security
KeyStore TWSServerKeyFile.jks
TrustStore TWSServerTrustFile.jks
DWC /opt/IBM/IWA/DWC/usr/servers/dwcServer/resources/security
KeyStore TWSServerKeyFile.jks
TrustStore TWSServerTrustFile.jks
TWSServerKeyStore.jks
This KeyStore contains the private and public certificates for the server, the Root and Intermediate public certificates of the CA that signed the server certificate. The public certificate of the server is exported and imported into the TWSServerTrustStore.jks and TWSClientKeyStore.
TWSServerTrustStore.jks
This TrustStore contains the public certificates for the server, the Root and Intermediate public certificates of the CA that signed the server certificate.
The following is a high-level procedure to replace the default certificates used by MDM and DWC.
- Create New KeyStore and TrustStore for the MDM
- Generate a Certificate Signing Request (CSR) for the MDM
- Send the CSR to the CA to be signed
- Receive the signed certificate and CA chain
- Import the signed certificate and CA chain into KeyStore
- Export the Public certificate from the KeyStore
- Create a new TrustStore for the MDM
- Import the Root, Intermediate, and the Public certificates of the server
- Replace Default KeyStore and TrustStore for MDM
- Replace Default KeyStore and TrustStore for DWC
The flow chart below depicts the procedure.
Update in version 9.5 Fix Pack 04
The new feature, Automatic deployment of security certificates on agents, introduced in version 9.5 Fix Pack 04 applies to Dynamic Agents only and doesn’t affect the above process flow. One requirement that must be met is that certificates for all components, i.e., MDM, DWC, and DAs, must be signed by the same CA.
The following sections describe how to create and populate new KeyStore and TrustStore with the required private and public certificates of the MDM and DWC.
1.2.1 Create New KeyStore for MDM
Follow the steps below to replace the default certificates for the MDM and DWC.
2. Create a new KeyStore for the MDM
cd /home/iwadmin/certs
keytool -genkey -keyalg RSA -sigalg SHA256withRSA -keysize 2048 -validity 3650 -alias whaleshark.aquarium.com -keystore IWAServerKeyStore.jks
Enter keystore password: <Enter a Password>
Re-enter new password: <Enter the same Password>
What is your first and last name?
[Unknown]: whaleshark.aquarium.com
What is the name of your organizational unit?
[Unknown]: BatchOps
What is the name of your organization?
[Unknown]: Aquarium
What is the name of your City or Locality?
[Unknown]: MarianaTrench
What is the name of your State or Province?
[Unknown]: PacificOcean
What is the two-letter country code for this unit?
[Unknown]: US
Is CN=whaleshark.aquarium.com, OU=BatchOps, O=Aquarium, L=MarianaTrench, ST=PacificOcean, C=US correct?
[no]: yes
Enter key password for <mykey>
(RETURN if same as keystore password): <Enter>
The key password must be the same as the store password. Even though JKS allows them to be different, WA only use one password to open both.
1.2.2 Generate a CSR for MDM
Follow the steps below to create a Certificate Signing Request (CSR) for the MDM
2. Send the CSR to the CA to be signed. The CA signs the certificate and sends back the signed certificate along with the Root and Intermediate certificates.
whaleshark.crt
intermediate.cer
AquariumRoot.cer 3. Import the certificates in the order shown below. a. keytool -importcert -file AquariumRoot.cer -keystore IWAServerKeyStore.jks -alias root.cert -trustcacerts
Enter keystore password: <Enter the Password used when the KeyStore was created>
…
…
Trust this certificate? [no]: yes
b. keytool -importcert -file intermediate.cer -keystore IWAServerKeyStore.jks -alias intermediate.cert -trustcacerts
c. keytool -importcert -file whaleshark.cer -keystore IWAServerKeyStore.jks -alias whaleshark.aquarium.com -trustcacerts
4. View the contents of the KeyStore
keytool -list -keystore IWAServerKeyStore.jks
Keystore type: jks
Keystore provider: SUN
Your keystore contains 3 entries
intermediate.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:65:AC:DC:A4:D8:C3:8A:54:23:72:59:3D:C6:41:D5:79:1D:CB:A9
whaleshark.aquarium.com, Dec 5, 2019, PrivateKeyEntry,
Certificate fingerprint (SHA1): CD:AE:BC:D2:7A:4D:37:A9:3D:24:29:45:1A:72:B3:45:2C:67:3A:56
root.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:FA:EC:28:A6:23:D1:AC:49:24:D4:A3:36:AF:2C:28:4C:AC:79:B4
5. Export the Public Key into a file from the KeyStore keytool -exportcert -alias whaleshark.aquarium.com -file whaleshark.pub.cer -keystore IWAServerKeyStore.jks -storetype jks
1.2.3 Create New TrustStore for MDM
Follow the steps below to create a new TrustStore for the MDM.
keytool -genkey -keyalg RSA -sigalg SHA256withRSA -keysize 2048 -validity 3650 -keystore IWAServerTrustStore.jks
Enter keystore password: <Enter the Password used when the KeyStore was created>
Re-enter new password: <Enter the Password used when the KeyStore was created>
What is your first and last name?
[Unknown]: whaleshark.aquarium.com
What is the name of your organizational unit?
[Unknown]: BatchOps
What is the name of your organization?
[Unknown]: Aquarium
What is the name of your City or Locality?
[Unknown]: MarianaTrench
What is the name of your State or Province?
[Unknown]: PacificOcean
What is the two-letter country code for this unit?
[Unknown]: US
Is CN=whaleshark.aquarium.com, OU=BatchOps, O=Aquarium, L=MarianaTrench, ST=PacificOcean, C=US correct?
[no]: yes
Enter key password for <mykey>
(RETURN if same as keystore password):
2. Import the Root, Intermediate, and the Public Key of the server certificates in the order shown below.
a. keytool -importcert -file AquariumRoot.cer -keystore IWAServerTrustStore.jks -alias root.cert -trustcacertsEnter keystore password: <Enter the Password used when the KeyStore was created>
…
…
Trust this certificate? [no]: yes
b. keytool -importcert -file intermediate.cer -keystore IWAServerTrustStore.jks -alias intermediate.cert -trustcacerts
c. keytool -importcert -file whaleshark.pub.cer -keystore IWAServerTrustStore.jks -alias whaleshark.pub -trustcacerts
3. View the contents of the TrustStore
keytool -list -keystore IWAServerTrustStore.jks
Enter keystore password: <Enter the Password used when the KeyStore was created>
Keystore type: jks
Keystore provider: SUN
Your keystore contains 4 entries
Enter keystore password:
Keystore type: jks
Keystore provider: SUN
Your keystore contains 4 entries
whaleshark.pub, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): CD:AE:BC:D2:7A:4D:37:A9:3D:24:29:45:1A:72:B3:45:2C:67:3A:56
intermediate.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:65:AC:DC:A4:D8:C3:8A:54:23:72:59:3D:C6:41:D5:79:1D:CB:A9
root.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:FA:EC:28:A6:23:D1:AC:49:24:D4:A3:36:AF:2C:28:4C:AC:79:B4
mykey, Dec 5, 2019, PrivateKeyEntry,
Certificate fingerprint (SHA1): EF:49:AB:47:AC:A3:49:4A:C4:0C:51:78:23:58:87:22:3A:BC:A4:B5
1.2.4 Replace Default KeyStore and TrustStore for MDM
Follow the steps below to replace the default KeyStore and TrustStore for the MDM.
2. Copy the new KeyStore and TrustStore
cp /home/iwadmin/certs/IWAServer* .
ls -l
-rw-r--r--. 1 iwadmin iwadmin 5507 Nov 12 20:02 IWAServerKeyStore.jks
-rw-r--r--. 1 iwadmin iwadmin 6465 Nov 12 21:07 IWAServerTrustStore.jks
-rw-------. 1 iwadmin iwadmin 897 Jul 15 17:20 ltpa.keys
-rw-------. 1 iwadmin iwadmin 897 Jul 15 17:20 ltpa.keys.orig
-rw-r--r--. 1 iwadmin iwadmin 4503 Nov 12 21:48 TWSServerKeyFile.jks
-rw-r--r--. 1 iwadmin iwadmin 118579 Nov 12 21:48 TWSServerTrustFile.jks
3. Encrypt the password for the KeyStore and TrustStore
cd /opt/IBM/IWA/WLP/bin
./securityUtility encode <Enter the Password used when the KeyStore was created>
{xor}Afhw!cbW5DL%#
4. Copy the encrypted password and update it in the ssl_variables along with references to the new KeyStore and TrustStore
cd /opt/IBM/IWA/IWS/usr/servers/engineServer/configDropins/overrides
cp ssl_variables.xml ssl_variables.xml.orig
vi ssl_variables.xml
Update the values shown in Bold
<server description="ssl_variables">
<variable name="keyStore.location" value="IWAServerKeyStore.jks"/>
<variable name="keyStore.password" value="{xor}Afhw!cbW5DL%#"/>
<variable name="keyStore.type" value="JKS"/>
<variable name="trustStore.location" value="IWAServerTrustStore.jks"/>
<variable name="trustStore.password" value="{xor}Afhw!cbW5DL%#"/>
<variable name="trustStore.type" value="JKS"/>
</server>
5. Save and exit.
6. The changes are effective immediately and doesn’t require the MDM to be restarted.
1.2.5 Replace Default KeyStore and TrustStore for the DWC
Follow the steps below to replace the default KeyStore and TrustStore for DWC and Backup DWC.
2. Copy the new KeyStore and TrustStore
cp /home/iwadmin/certs/IWAServer* .
ls -l
-rw-r--r--. 1 iwadmin iwadmin 5507 Nov 12 20:02 IWAServerKeyStore.jks
-rw-r--r--. 1 iwadmin iwadmin 6465 Nov 12 21:07 IWAServerTrustStore.jks
-rw-------. 1 iwadmin iwadmin 897 Jul 15 17:20 ltpa.keys
-rw-r--r--. 1 iwadmin iwadmin 4503 Nov 12 21:48 TWSServerKeyFile.jks
-rw-r--r--. 1 iwadmin iwadmin 118579 Nov 12 21:48 TWSServerTrustFile.jks
3. Copy the encrypted password and update it in the ssl_variables along with references to the new KeyStore and TrustStore
7cd /opt/IBM/IWA/DWC/usr/servers/dwcServer/configDropins/overrides
cp ssl_variables.xml ssl_variables.xml.orig
vi ssl_variables.xml
Update the values shown in Bold
<server description="ssl_variables">
<variable name="keyStore.location" value="IWAServerKeyStore.jks"/>
<variable name="keyStore.password" value="{xor}Afhw!cbW5DL%#"/>
<variable name="keyStore.type" value="JKS"/>
<variable name="trustStore.location" value="IWAServerTrustStore.jks"/>
<variable name="trustStore.password" value="{xor}Afhw!cbW5DL%#"/>
<variable name="trustStore.type" value="JKS"/>
</server>
4. Save and exit.
5. The changes are effective immediately and doesn’t require the DWC to be restarted
1.2.6 Verify that DWC is using the new Certificate
Follow the steps below to verify that the DWC is using the new CA signed certificates.
2. In the address bar, click on the padlock next to the URL. The icon may be different based on the browser being used.
3. Click on View Certificate and verify that the following information is shown.
The new feature, Automatic deployment of security certificates on agents, introduced in version 9.5 Fix Pack 04 applies to Dynamic Agents only and doesn’t affect the above process flow. One requirement that must be met is that certificates for all components, i.e., MDM, DWC, and DAs, must be signed by the same CA.
The following sections describe how to create and populate new KeyStore and TrustStore with the required private and public certificates of the MDM and DWC.
1.2.1 Create New KeyStore for MDM
Follow the steps below to replace the default certificates for the MDM and DWC.
- Login as iwadmin and set the PATH variable to include the key management tool, keytool, provided by WA
2. Create a new KeyStore for the MDM
cd /home/iwadmin/certs
keytool -genkey -keyalg RSA -sigalg SHA256withRSA -keysize 2048 -validity 3650 -alias whaleshark.aquarium.com -keystore IWAServerKeyStore.jks
Enter keystore password: <Enter a Password>
Re-enter new password: <Enter the same Password>
What is your first and last name?
[Unknown]: whaleshark.aquarium.com
What is the name of your organizational unit?
[Unknown]: BatchOps
What is the name of your organization?
[Unknown]: Aquarium
What is the name of your City or Locality?
[Unknown]: MarianaTrench
What is the name of your State or Province?
[Unknown]: PacificOcean
What is the two-letter country code for this unit?
[Unknown]: US
Is CN=whaleshark.aquarium.com, OU=BatchOps, O=Aquarium, L=MarianaTrench, ST=PacificOcean, C=US correct?
[no]: yes
Enter key password for <mykey>
(RETURN if same as keystore password): <Enter>
The key password must be the same as the store password. Even though JKS allows them to be different, WA only use one password to open both.
1.2.2 Generate a CSR for MDM
Follow the steps below to create a Certificate Signing Request (CSR) for the MDM
- Generate a Certificate Signing Request CSR for the MDM server.
2. Send the CSR to the CA to be signed. The CA signs the certificate and sends back the signed certificate along with the Root and Intermediate certificates.
whaleshark.crt
intermediate.cer
AquariumRoot.cer 3. Import the certificates in the order shown below. a. keytool -importcert -file AquariumRoot.cer -keystore IWAServerKeyStore.jks -alias root.cert -trustcacerts
Enter keystore password: <Enter the Password used when the KeyStore was created>
…
…
Trust this certificate? [no]: yes
b. keytool -importcert -file intermediate.cer -keystore IWAServerKeyStore.jks -alias intermediate.cert -trustcacerts
c. keytool -importcert -file whaleshark.cer -keystore IWAServerKeyStore.jks -alias whaleshark.aquarium.com -trustcacerts
4. View the contents of the KeyStore
keytool -list -keystore IWAServerKeyStore.jks
Keystore type: jks
Keystore provider: SUN
Your keystore contains 3 entries
intermediate.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:65:AC:DC:A4:D8:C3:8A:54:23:72:59:3D:C6:41:D5:79:1D:CB:A9
whaleshark.aquarium.com, Dec 5, 2019, PrivateKeyEntry,
Certificate fingerprint (SHA1): CD:AE:BC:D2:7A:4D:37:A9:3D:24:29:45:1A:72:B3:45:2C:67:3A:56
root.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:FA:EC:28:A6:23:D1:AC:49:24:D4:A3:36:AF:2C:28:4C:AC:79:B4
5. Export the Public Key into a file from the KeyStore keytool -exportcert -alias whaleshark.aquarium.com -file whaleshark.pub.cer -keystore IWAServerKeyStore.jks -storetype jks
1.2.3 Create New TrustStore for MDM
Follow the steps below to create a new TrustStore for the MDM.
- Create a new TrustStore for the MDM and provide the same responses as the KeyStore
keytool -genkey -keyalg RSA -sigalg SHA256withRSA -keysize 2048 -validity 3650 -keystore IWAServerTrustStore.jks
Enter keystore password: <Enter the Password used when the KeyStore was created>
Re-enter new password: <Enter the Password used when the KeyStore was created>
What is your first and last name?
[Unknown]: whaleshark.aquarium.com
What is the name of your organizational unit?
[Unknown]: BatchOps
What is the name of your organization?
[Unknown]: Aquarium
What is the name of your City or Locality?
[Unknown]: MarianaTrench
What is the name of your State or Province?
[Unknown]: PacificOcean
What is the two-letter country code for this unit?
[Unknown]: US
Is CN=whaleshark.aquarium.com, OU=BatchOps, O=Aquarium, L=MarianaTrench, ST=PacificOcean, C=US correct?
[no]: yes
Enter key password for <mykey>
(RETURN if same as keystore password):
2. Import the Root, Intermediate, and the Public Key of the server certificates in the order shown below.
a. keytool -importcert -file AquariumRoot.cer -keystore IWAServerTrustStore.jks -alias root.cert -trustcacertsEnter keystore password: <Enter the Password used when the KeyStore was created>
…
…
Trust this certificate? [no]: yes
b. keytool -importcert -file intermediate.cer -keystore IWAServerTrustStore.jks -alias intermediate.cert -trustcacerts
c. keytool -importcert -file whaleshark.pub.cer -keystore IWAServerTrustStore.jks -alias whaleshark.pub -trustcacerts
3. View the contents of the TrustStore
keytool -list -keystore IWAServerTrustStore.jks
Enter keystore password: <Enter the Password used when the KeyStore was created>
Keystore type: jks
Keystore provider: SUN
Your keystore contains 4 entries
Enter keystore password:
Keystore type: jks
Keystore provider: SUN
Your keystore contains 4 entries
whaleshark.pub, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): CD:AE:BC:D2:7A:4D:37:A9:3D:24:29:45:1A:72:B3:45:2C:67:3A:56
intermediate.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:65:AC:DC:A4:D8:C3:8A:54:23:72:59:3D:C6:41:D5:79:1D:CB:A9
root.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:FA:EC:28:A6:23:D1:AC:49:24:D4:A3:36:AF:2C:28:4C:AC:79:B4
mykey, Dec 5, 2019, PrivateKeyEntry,
Certificate fingerprint (SHA1): EF:49:AB:47:AC:A3:49:4A:C4:0C:51:78:23:58:87:22:3A:BC:A4:B5
1.2.4 Replace Default KeyStore and TrustStore for MDM
Follow the steps below to replace the default KeyStore and TrustStore for the MDM.
- Go to the directory where the default KeyStore and TrustStores are located
2. Copy the new KeyStore and TrustStore
cp /home/iwadmin/certs/IWAServer* .
ls -l
-rw-r--r--. 1 iwadmin iwadmin 5507 Nov 12 20:02 IWAServerKeyStore.jks
-rw-r--r--. 1 iwadmin iwadmin 6465 Nov 12 21:07 IWAServerTrustStore.jks
-rw-------. 1 iwadmin iwadmin 897 Jul 15 17:20 ltpa.keys
-rw-------. 1 iwadmin iwadmin 897 Jul 15 17:20 ltpa.keys.orig
-rw-r--r--. 1 iwadmin iwadmin 4503 Nov 12 21:48 TWSServerKeyFile.jks
-rw-r--r--. 1 iwadmin iwadmin 118579 Nov 12 21:48 TWSServerTrustFile.jks
3. Encrypt the password for the KeyStore and TrustStore
cd /opt/IBM/IWA/WLP/bin
./securityUtility encode <Enter the Password used when the KeyStore was created>
{xor}Afhw!cbW5DL%#
4. Copy the encrypted password and update it in the ssl_variables along with references to the new KeyStore and TrustStore
cd /opt/IBM/IWA/IWS/usr/servers/engineServer/configDropins/overrides
cp ssl_variables.xml ssl_variables.xml.orig
vi ssl_variables.xml
Update the values shown in Bold
<server description="ssl_variables">
<variable name="keyStore.location" value="IWAServerKeyStore.jks"/>
<variable name="keyStore.password" value="{xor}Afhw!cbW5DL%#"/>
<variable name="keyStore.type" value="JKS"/>
<variable name="trustStore.location" value="IWAServerTrustStore.jks"/>
<variable name="trustStore.password" value="{xor}Afhw!cbW5DL%#"/>
<variable name="trustStore.type" value="JKS"/>
</server>
5. Save and exit.
6. The changes are effective immediately and doesn’t require the MDM to be restarted.
1.2.5 Replace Default KeyStore and TrustStore for the DWC
Follow the steps below to replace the default KeyStore and TrustStore for DWC and Backup DWC.
- Go to the directory where the default KeyStore and TrustStores are located
2. Copy the new KeyStore and TrustStore
cp /home/iwadmin/certs/IWAServer* .
ls -l
-rw-r--r--. 1 iwadmin iwadmin 5507 Nov 12 20:02 IWAServerKeyStore.jks
-rw-r--r--. 1 iwadmin iwadmin 6465 Nov 12 21:07 IWAServerTrustStore.jks
-rw-------. 1 iwadmin iwadmin 897 Jul 15 17:20 ltpa.keys
-rw-r--r--. 1 iwadmin iwadmin 4503 Nov 12 21:48 TWSServerKeyFile.jks
-rw-r--r--. 1 iwadmin iwadmin 118579 Nov 12 21:48 TWSServerTrustFile.jks
3. Copy the encrypted password and update it in the ssl_variables along with references to the new KeyStore and TrustStore
7cd /opt/IBM/IWA/DWC/usr/servers/dwcServer/configDropins/overrides
cp ssl_variables.xml ssl_variables.xml.orig
vi ssl_variables.xml
Update the values shown in Bold
<server description="ssl_variables">
<variable name="keyStore.location" value="IWAServerKeyStore.jks"/>
<variable name="keyStore.password" value="{xor}Afhw!cbW5DL%#"/>
<variable name="keyStore.type" value="JKS"/>
<variable name="trustStore.location" value="IWAServerTrustStore.jks"/>
<variable name="trustStore.password" value="{xor}Afhw!cbW5DL%#"/>
<variable name="trustStore.type" value="JKS"/>
</server>
4. Save and exit.
5. The changes are effective immediately and doesn’t require the DWC to be restarted
1.2.6 Verify that DWC is using the new Certificate
Follow the steps below to verify that the DWC is using the new CA signed certificates.
- Launch a Browser and go to the following URL
2. In the address bar, click on the padlock next to the URL. The icon may be different based on the browser being used.
3. Click on View Certificate and verify that the following information is shown.
1.2.7 Update Dynamic Workload Broker Workstation Properties
In order to work with the Dynamic Agents through the Dynamic Workload Broker (DWB), such as, delete and extract, the CN names of the CA signed certificates need to be added to the Broker.AuthorizedCNs property in BrokerWorkstation.properties file.
Follow the steps below to update this file.
2. Edit the BrokerWorkstation.properties file and append the values shown in bold below vi BrokerWorkstation.properties
Broker.AuthorizedCNs=Server;ServerNew;whaleshark.aquarium.com;intermediate
3. Restart the MDM WLP cd /opt/IBM/IWA/IWS/appservertools
./stopAppServer.sh
./startAppServer.sh
1.3 Replacing Certificates used by DA
The Dynamic Agent uses two KeyStores, one in CMS format (kdb extension) and the other in JKS format (jks extension). Both KeyStores contain the same certificates, which include the private certificate for the server where the agent is installed, the public certificate of the MDM server, the Root and Intermediate public certificates of the CA that signed the MDM server’s certificate. The public certificate of the server where the agent is installed is exported from one of the above KeyStores and imported into the MDM and BKM servers TrustStores. They are located in the following directory:
/opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert
CMS KeyStore TWSClientKeyStore.kdb
JKS KeyStore TWSClientKeyStoreJKS.jks
In order to simplify and repeat the process of renewing the certificates when they expire, the following procedure is used to replace the certificates used by DA.
In order to work with the Dynamic Agents through the Dynamic Workload Broker (DWB), such as, delete and extract, the CN names of the CA signed certificates need to be added to the Broker.AuthorizedCNs property in BrokerWorkstation.properties file.
Follow the steps below to update this file.
- Go to the directory where the BrokerWorkstation.properties file is located
2. Edit the BrokerWorkstation.properties file and append the values shown in bold below vi BrokerWorkstation.properties
Broker.AuthorizedCNs=Server;ServerNew;whaleshark.aquarium.com;intermediate
3. Restart the MDM WLP cd /opt/IBM/IWA/IWS/appservertools
./stopAppServer.sh
./startAppServer.sh
1.3 Replacing Certificates used by DA
The Dynamic Agent uses two KeyStores, one in CMS format (kdb extension) and the other in JKS format (jks extension). Both KeyStores contain the same certificates, which include the private certificate for the server where the agent is installed, the public certificate of the MDM server, the Root and Intermediate public certificates of the CA that signed the MDM server’s certificate. The public certificate of the server where the agent is installed is exported from one of the above KeyStores and imported into the MDM and BKM servers TrustStores. They are located in the following directory:
/opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert
CMS KeyStore TWSClientKeyStore.kdb
JKS KeyStore TWSClientKeyStoreJKS.jks
In order to simplify and repeat the process of renewing the certificates when they expire, the following procedure is used to replace the certificates used by DA.
- For the DA installed on the MDM, generate a CSR from the CMS TWSClientKeyStore.kdb
- Send the CSR to the CA to be signed
- Receive the CA signed certificate
- Import the root, intermediate, and the CA signed certificate into the CMS TWSClientKeyStore.kdb
- Import the public certificate of the MDM into the CMS TWSClientKeyStore.kdb
- Export the public certificate of the DA from the CMS TWSClientKeyStore.kdb
- Import the public certificate of the DA into the JKS IWAServerTrustStore.jks
- Restart the MDM
- Convert the CMS TWSClientKeyStore.kdb to JKS TWSClientKeyStore.jks
- Update the certificate related parameters in ita.ini of the DA
- Restart the DA and verify connectivity by running a test job
Update in version 9.5 Fix Pack 04
The new feature, Automatic deployment of security certificates on agents, introduced in version 9.5 Fix Pack 04 applies to Dynamic Agents and simplifies the above process by eliminating steps 4-10. Steps 1-3 must still be completed, and the certificates must be placed in the certificate depot location, <TWSDATA>/TWS/ssl/depot. This dir only exists if a fresh installation was performed using FP4 image. If an existing installation was upgraded to FP4, this directory needs to be created. The certificates are downloaded to an agent in the following scenarios:
The following sections describe how to replace the default certificates used by the DA.
1.3.1 Generate a CSR for the DA in the CMS TWSClientKeyStore
Follow the steps below to generate and update the CMS TWSClientKeyStore.kdb
2. Source the script to set the environment as shown below.
. /opt/IBM/IWA/TWS/tws_env.sh
3. Backup the existing TWSClientKeyStores
cd /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert
cp TWSClientKeyStore.kdb TWSClientKeyStore.kdb.orig
cp TWSClientKeyStoreJKS.jks TWSClientKeyStoreJKS.jks.orig
4. Generate a CSR from the CMS TWSClientKeyStore.kdb
gsk8capicmd_64 -certreq -create -sigalg SHA256withRSA -size 2048 -db TWSClientKeyStore.kdb -label agent -dn "CN=agent.aquarium.com,OU=BatchOps,O=Aquarium,L=MarianaTrench,ST=PacificOcean,C=US" -file agent.csr -stashed
5. Send the CSR, agent.csr, to the CA to be signed and returned.
6. Once the CA signed certificate is received, import it into the CMS TWSClientKeyStore.kdb along with the root, intermediate, and MDM server’s public certificate in the order shown below
a. gsk8capicmd_64 -cert -add -db TWSClientKeyStore.kdb -file /home/iwadmin/certs/AquariumRoot.cer -label root.cert -trust enable -stashed
b. gsk8capicmd_64 -cert -add -db TWSClientKeyStore.kdb -file /home/iwadmin/certs/intermediate.cer -label intermediate.cert -trust enable -stashed
c. gsk8capicmd_64 -cert -add -db TWSClientKeyStore.kdb -file /home/iwadmin/certs/whaleshark.pub.cer -label whaleshark.pub -trust enable -stashed
d. gsk8capicmd_64 -cert -receive -db TWSClientKeyStore.kdb -file /opt/IBM/IWA/TWSDATA/ITA/cpa/ita/cert/agent.cer -default_cert yes -stashed
7. Delete the following default certificates
a. gsk8capicmd_64 -cert -delete -db TWSClientKeyStore.kdb -label client
b. gsk8capicmd_64 -cert -delete -db TWSClientKeyStore.kdb -label server
c. gsk8capicmd_64 -cert -delete -db TWSClientKeyStore.kdb -label serverold
8. Extract the public certificate for the agent and copy it to the MDM
gsk8capicmd_64 -cert -extract -db TWSClientKeyStore.kdb -stashed -label agent -target agent.pub.crt
cp agent.pub.crt /home/iwadmin/certs
9. View the contents of the KeyStore
gsk8capicmd_64 -cert -list -db TWSClientKeyStore.kdb
Source database passwordCertificates found
Certificates found
* default, - personal, ! trusted, # secret key
! root.cert
! intermediate.cert
! whaleshark.pub
- agent
1.3.2 Import the public certificate of the DA into the MDM TrustStore
Follow the steps below to Import the public certificate of the DA into the JKS IWAServerTrustStore.jks.
cd /opt/IBM/IWA/IWS/usr/servers/engineServer/resources/security
cp IWAServerTrustStore.jks IWAServerTrustStore.jks.orig
2. Import the public certificate of the DA into the Primary MDM server’s TrustStore
keytool -importcert -file /home/iwadmin/certs/agent.pub.crt -keystore /opt/IBM/IWA/IWS/usr/servers/engineServer/resources/security/IWAServerTrustStore.jks -alias agent.pub -trustcacerts
3. View the Certificates in the Server TrustStore
keytool -list -keystore /opt/IBM/IWA/IWS/usr/servers/engineServer/resources/security/IWAServerTrustStore.jks -storepass iwa4aquarium
Enter Keystore Password:
Keystore type: jks
Keystore provider: SUN
Your keystore contains 5 entries
whaleshark.pub, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): CD:AE:BC:D2:7A:4D:37:A9:3D:24:29:45:1A:72:B3:45:2C:67:3A:56
intermediate.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:65:AC:DC:A4:D8:C3:8A:54:23:72:59:3D:C6:41:D5:79:1D:CB:A9
root.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:FA:EC:28:A6:23:D1:AC:49:24:D4:A3:36:AF:2C:28:4C:AC:79:B4
mykey, Dec 5, 2019, PrivateKeyEntry,
Certificate fingerprint (SHA1): EF:49:AB:47:AC:A3:49:4A:C4:0C:51:78:23:58:87:22:3A:BC:A4:B5
agent.pub, Dec 11, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 43:A8:C3:34:D3:EA:38:4B:D2:F7:38:40:3A:F4:CA:3A:51:7A:C3:F1
4. Restart the Primary MDM
cd /opt/IBM/IWA/IWS/appservertools
./stopAppServer.sh
./startAppServer.sh
1.3.3 Convert the CMS TWSClientKeyStore to JKS TWSClientKeyStore
Follow the steps below to convert the CMS TWSClientKeyStore to JKS TWSClientKeyStore.jks.
cp TWSClientKeyStoreJKS.jks TWSClientKeyStoreJKS.jks.orig
2. Delete any certificates with the extension, arm rm *.arm
3. Run the following command to convert the CMS TWSClientKeyStore to JKS format
/opt/IBM/IWA/IWS/TWS/_uninstall/ACTIONTOOLS/twsManageKey.sh --certPath /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert --jreBinPath /opt/IBM/IWA/IWS/TWS/JavaExt/jre/bin --gsKitDir /opt/IBM/IWA/IWS/TWS/tmpGSKit64/8 --envCmd /opt/IBM/IWA/IWS/TWS/tws_env.sh --itaIni /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/ita.ini
IBM Workload Scheduler Environment Successfully Set !!!
twsManageKey() executing: /opt/IBM/IWA/IWS/TWS/tmpGSKit64/8/bin/gsk8capicmd_64 -cert -extract -db /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStore.kdb -stashed -type cms -format ascii -target /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/ca_root.cert.arm -label root.cert
Certificate was added to keystore
twsManageKey() executing: /opt/IBM/IWA/IWS/TWS/JavaExt/jre/bin/keytool -importcert -keystore /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStoreP12.p12 -storepass default -storetype pkcs12 -file /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/ca_root.cert.arm -alias root.cert -noprompt
twsManageKey() executing: /opt/IBM/IWA/IWS/TWS/tmpGSKit64/8/bin/gsk8capicmd_64 -cert -extract -db /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStore.kdb -stashed -type cms -format ascii -target /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/ca_intermediate.cert.arm -label intermediate.cert
Certificate was added to keystore
twsManageKey() executing: /opt/IBM/IWA/IWS/TWS/JavaExt/jre/bin/keytool -importcert -keystore /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStoreP12.p12 -storepass default -storetype pkcs12 -file /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/ca_intermediate.cert.arm -alias intermediate.cert -noprompt
twsManageKey() executing: /opt/IBM/IWA/IWS/TWS/tmpGSKit64/8/bin/gsk8capicmd_64 -cert -extract -db /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStore.kdb -stashed -type cms -format ascii -target /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/ca_whaleshark.pub.arm -label whaleshark.pub
Certificate was added to keystore
twsManageKey() executing: /opt/IBM/IWA/IWS/TWS/JavaExt/jre/bin/keytool -importcert -keystore /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStoreP12.p12 -storepass default -storetype pkcs12 -file /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/ca_whaleshark.pub.arm -alias whaleshark.pub -noprompt
Importing keystore /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStoreP12.p12 to /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStoreJKS.jks...
Entry for alias agent successfully imported.
Entry for alias root.cert successfully imported.
Entry for alias intermediate.cert successfully imported.
Entry for alias whaleshark.pub successfully imported.
Import command completed: 4 entries successfully imported, 0 entries failed or cancelled
4. View the contents of the JKS ClientKeyStoreJKS. It should be identical to the CMS TWSClientKeyStore
keytool -list -keystore TWSClientKeyStoreJKS.jks -storepass default
Keystore type: jks
Keystore provider: SUN
Your keystore contains 4 entries
whaleshark.pub, Dec 11, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): CD:AE:BC:D2:7A:4D:37:A9:3D:24:29:45:1A:72:B3:45:2C:67:3A:56
intermediate.cert, Dec 11, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:65:AC:DC:A4:D8:C3:8A:54:23:72:59:3D:C6:41:D5:79:1D:CB:A9
agent, Dec 11, 2019, PrivateKeyEntry,
Certificate fingerprint (SHA1): 43:A8:C3:34:D3:EA:38:4B:D2:F7:38:40:3A:F4:CA:3A:51:7A:C3:F1
root.cert, Dec 11, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:FA:EC:28:A6:23:D1:AC:49:24:D4:A3:36:AF:2C:28:4C:AC:79:B4
1.3.4 Update the certificate related parameters in ita.ini of the DA
Follow the steps below to update the certificate related parameters in ita.ini of the DA.
2. Open ita.ini file, scroll down to the ITA SSL section and update and verify the following parameters shown in bold.
vi ita.ini
[ITA SSL]
gskit_dir = /usr/Tivoli/TWS/GSKit64/8/lib64
fips_enable = yes
password_file =
cert_label = agent
key_db_name = TWSClientKeyStore
key_repository_dir = /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert
gskit_libs_installed = 1
conn_verify = 1
ca_cert_fname = /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/cacert.pem
java_truststore_password_file = /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStoreJKS.sth
java_truststore_file = /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStoreJKS.jks
3. Save and exit.
1.3.5 Restart Agent and Verify
Follow the steps below to restart the agent and verify its connectivity to the MDM server.
./ShutDownLwa
./StartUpLwa
2. Login to the DWC and navigate to Monitor Workload, Workstation and make sure that it is linked and running.
3. If it not linked and running, check the agent’s logfile
cd /opt/IBM/IWA/TWSDATA/stdlist/JM/
tail JobManager_message.log
2019-11-13 15:43:10.351-05:00|2046801664|3225|<server_name>.aquarium.com|AWSITA081E The agent can not send the resource information to "https://<server_name>.aquarium.com:31116/JobManagerRESTWeb/JobScheduler/resource". The error is: "AWSITA245E An error occurred getting the response of the HTTP request. The error is "CURL error 35".".
4. Review the steps above and verify that each of the step is executed successfully.
5. If the agent is able to connect successfully to the MDM, the last message in the logfile indicates that it is able to send information to the MDM server.
2019-11-13 19:18:26.461-05:00|INFO|JobManager|18446744071629174528|30204|whaleshark.aquarium.com|AWSITA083I Resource information was sent to "https://whaleshark.aquarium.com:31116/JobManagerRESTWeb/JobScheduler/resource".
6. To verify two-way communication between the DA and MDM, submit a test job as follows:
a. Login as iwadmin to the MDM
b. Run conman in interactive mode conman
c. Create and submit a job on the fly sbd whaleshark_da#”echo Hello”;logon=iwadmin
d. Keep running the following command until the job completes successfully. sj whaleshark_da#JOBS.ECHO
e. If the job stays stuck in WAIT state, look at the joblog for any errors by running the following command. sj whaleshark_da#JOBS.ECHO;stdlist
f. Review the steps above and verify that each of the step is executed successfully.
g. Type e followed by an enter to exit conman.
7. Follow the steps in section 4.6 to replicate the TWS Client KeyStores on all DAs to enable SSL communication between MDM and DAs using CA signed certificates
1.4 Update the SSL settings of a DA
Follow the steps below to update the SSL settings of a Dynamic Agent
1.Logon to the server as iwadmin (Unix) or Aquarium\iwadmin (Windows) user
2.Copy the Cliet KeyStore files from the MDM server to the DA
Unix
cd /opt/IBM/IWA/TWSDATA/ITA/cpa/ita/cert
mkdir backup
cp TWSClient* backup
Run the following command with whaleshark (for Dev) or tws (for Prod)
scp iwadmin@whaleshark:/opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStore* .
The authenticity of host 'whaleshark.aquarium.com (10.150.35.59)' can't be established.
ECDSA key fingerprint is SHA256:Xwo1hl+qLUsLx5EPpSvatBQVNbn89frtabLOao5QpWQ.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'whaleshark.aquarium.com,10.150.35.59' (ECDSA) to the list of known hosts.
iwadmin@whaleshark.aquarium.com's password: <enter password for iwadmin>
TWSClientKeyStore.kdb 100% 20KB 12.0MB/s 00:00
TWSClientKeyStore.sth 100% 129 182.5KB/s 00:00
TWSClientKeyStoreJKS.jks 100% 11KB 5.2MB/s 00:00
TWSClientKeyStoreJKS.sth 100% 129 98.6KB/s 00:00
Windows
cd \IBM\IWA\TWS\ITA\cpa\ita\cert
mkdir backup
copy TWSClient* backup
Launch Winscp and connect to whaleshark (for Dev) or tws (for Prod) as iwadmin
Copy the following files from the whaleshark or tws to the DA
From Dir: /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert
To Dir: \IBM\IWA\TWS\ITA\cpa\ita\cert
Files: TWSClientKeyStore.kdb
TWSClientKeyStore.sth
TWSClientKeyStoreJKS.jks
TWSClientKeyStoreJKS.sth
3. Go to the following directory and edit ita.ini
Unix
cd /opt/IBM/IWA/TWSDATA/ITA/cpa/ita
vi ita.ini
Windows
cd \IBM\IWA\TWS\ITA\cpa\ita
notepad ita.ini
4.Make the following changes
ssl_port=32114
cert_label=agent
Add the following new settings
sslv3_cipher = NONE
tls10_cipher = NONE
tls11_cipher = NONE
tls12_cipher = DFLT
1.5 Enable a DA
When an FTA was installed, the DA was also installed, but not enabled. Follow the steps below to enable the DA.
1.Logon to the server as iwadmin (Unix) or Aquarium\iwadmin (Windows) user
2. Go to the following directory and edit JobManager.ini
Unix
cd /opt/IBM/IWA/TWSDATA/ITA/cpa/config
vi JobManager.ini
Windows
cd \IBM\IWA\TWS\ITA\cpa\config
notepad JobManager.ini
3.Make the following changes in bold
ThisWorkstation = <short_hostnem>_DA
FullyQualifiedHostname = <short_hostnem>.aquarium.com
ResourceAdvisorUrl = https://whaleshark.aquarium.com:32116/JobManagerRESTWeb/JobScheduler/resource (for Dev)
https://iwa.aquarium.com:32116/JobManagerRESTWeb/JobScheduler/resource (for Prod)
ComputerSystemDisplayName = <short_hostnem>_DA
4.Start the DA
Unix
cd /opt/IBM/IWA/TWS
./StartUpLwa
Windows
cd \IBM\IWA\TWS
StartUpLwa
5.Verify that the DA is registered with the server. If it doesn’t show, give it a few minutes and run the following command again.
Login as iwadmin on whaleshark (for Dev) or tws (for Prod)
conman sc <short_hostnem>_DA
1.6 Prepare the MDM for SSL between MDM <> FTA
Follow the steps below to enable SSL between MDM and FTA communication.
1.If communication between the MDM and FTA also needs to be ecncrypted with custom certificates, then the following certificates need to be acquired:
TWSClient.key A private key of the certificate for the FTA, in PEM format
TWSClient.cer The CA signed certificate for the FTA, in PEM format
password.sth The password to access the private key, TWSClient.key, in
base64
TWSTrustCertificates.cer The certificates of all CAs that the FTA needs to trust
(i.e. both the Root and Intermediate CA), in PEM format
2.Place the above custom certificates in the following dir on the MDM. Note that the IBM self-signed certificates are already provided in the same dir. Replace them with the custom certificates.
/opt/IBM/IWA/IWS/TWS/ssl/OpenSSL
3.Logon to the MDM server, whaleshark, as iwadmin user
4. Go to the following directory and edit localopts
cd /opt/IBM/IWA/TWSDATA
vi localopts
5.Make the following changes in bold
nm SSL port =32113
SSL key ="/opt/IBM/IWA/IWS/TWS/ssl/OpenSSL/TWSClient.key"
SSL certificate ="/opt/IBM/IWA/IWS/TWS/ssl/OpenSSL/TWSClient.cer"
SSL key pwd ="/opt/IBM/IWA/IWS/TWS/ssl/OpenSSL/password.sth"
SSL CA certificate ="/opt/IBM/IWA/IWS/TWS/ssl/OpenSSL/TWSTrustCertificates.cer"
SSL random seed ="/opt/IBM/IWA/IWS/TWS/ssl/OpenSSL/TWS.rnd"
SSL Encryption Cipher =TLSv1.2
CLI SSL cipher=TLSv1.2
6.Update the Workstation definition of the MDM with the following settings in bold.
CPUNAME WHALESHARK
DESCRIPTION "This workstation is the Master Domain Manager (MDM)"
OS UNIX
NODE whaleshark.aquarium.com TCPADDR 32111
SECUREADDR 32113
TIMEZONE America/Bogota
DOMAIN MASTERDM
FOR MAESTRO
TYPE MANAGER
AUTOLINK ON
BEHINDFIREWALL OFF
SECURITYLEVEL ENABLED
FULLSTATUS ON
END
7.Update the Workstation definition of each FTA with the following settings in bold. For example, the definition of the FTA, GLOWFISH, is shownn below. Do not modify the definitions of the MASTERAGENTS, WHALESHARK_DWB, and WHALESHARK_DA
composer cr all.workstations.txt from ws=@
CPUNAME GLOWFISH
OS WNT
NODE glowfish.aquarium.com TCPADDR 32111
SECUREADDR 32113
TIMEZONE America/Bogota
DOMAIN MASTERDM
FOR MAESTRO
TYPE FTA
AUTOLINK ON
BEHINDFIREWALL OFF
SECURITYLEVEL ON
FULLSTATUS OFF
END
8.Reimport all modified FTA definitions
composer replace all.workstations.txt
9.Update the plan so that all updated FTA definitions are reflected in the plan.
optman chg cf = all
JnextPlan -for 0000
optman chg cf = yes
10.Stop the MDM
conman “stop;wait”
conman “shut;wait”
11.Start the MDM
cd /opt/IBM/IWA/IWS/TWS
./StartUp
conman start
12. Verify that optman and composer can run successfully.
optman ls
composer li vt=main_table
1.7 Update the SSL settings of an FTA
Follow the steps below to update the SSL settings in localopts of the Fault-Tolerant Agent (FTA).
1.If communication between the MDM and FTA also needs to be ecncrypted with custom certificates, then the following certificates need to be acquired:
TWSClient.key A private key of the certificate for the FTA, in PEM format
TWSClient.cer The CA signed certificate for the FTA, in PEM format
password.sth The password to access the private key, TWSClient.key, in
base64
TWSTrustCertificates.cer The certificates of all CAs that the FTA needs to trust
(i.e. both the Root and Intermediate CA), in PEM format
2.Place the above custom certificates in the following dir on the FTA. Note that the IBM self-signed certificates are already provided in the same dir. Replace them with the custom certificates.
/opt/IBM/IWA/IWS/TWS/ssl/OpenSSL
3.Logon to the server as iwadmin (Unix) or Aquarium\iwadmin (Windows) user
4. Go to the following directory and edit localopts
Unix
cd /opt/IBM/IWA/TWSDATA
vi localopts
Windows
cd \IBM\IWA\TWS
notepad localopts
5. Make the following changes in bold
Both
nm SSL port =32113
Unix
SSL key ="/opt/IBM/IWA/TWS/ssl/OpenSSL/TWSClient.key"
SSL certificate ="/opt/IBM/IWA/TWS/ssl/OpenSSL/TWSClient.cer"
SSL key pwd ="/opt/IBM/IWA/TWS/ssl/OpenSSL/password.sth"
SSL CA certificate ="/opt/IBM/IWA/TWS/ssl/OpenSSL/TWSTrustCertificates.cer"
SSL random seed ="/opt/IBM/IWA/TWS/ssl/OpenSSL/TWS.rnd"
Windows
SSL key ="C:\IBM\IWA\TWS\ssl\OpenSSL\TWSClient.key"
SSL certificate ="C:\IBM\IWA\TWS\ssl\OpenSSL\TWSClient.cer"
SSL key pwd ="C:\IBM\IWA\TWS\ssl\OpenSSL\password.sth"
SSL CA certificate ="C:\IBM\IWA\TWS\ssl\OpenSSL\TWSTrustCertificates.cer"
SSL random seed ="C:\IBM\IWA\TWS\ssl\OpenSSL\TWS.rnd"
Both
SSL Encryption Cipher =TLSv1.2
CLI SSL cipher=TLSv1.2
6. Stop the FTA
conman “stop;wait”
conman “shut;wait”
7. Start the FTA
Unix
cd /opt/IBM/IWA/TWS
./StartUp
conman link [whaleshark for Dev or tws for Prod]
conman start
Windows
cd \IBM\IWA\TWS
StartUp
conman link [whaleshark for Dev or tws for Prod]
conman start
8. Verify that composer can be run successfully. composer li vt=main_table
9.Verify that the FTA linked with the server successfully and it shows all the flags, LTI JW, as shown below as an example for GLOWFISH
Login as iwadmin on whaleshark (for Dev) or tws (for Prod)
conman sc <short_hostnem>
GLOWFISH 12 WIN FTA 10 0 03/18/20 23:59 LTI JW MASTERDM
2 Renewing the Expired Certificate of the MDM & DWC
The CA signed certificates start expiring from Nov 20, 2020. As such, these certificates must be renewed ahead of time in order to keep the various components communicating with each other and not interrupt the execution of the workload automation.
Follow the steps below to renew the Certificates for the MDM and DWC.
3. Generate a Certificate Signing Request CSR for the MDM server.
keytool -certreq -sigalg SHA256withRSA -alias whaleshark.aquarium.com -file whaleshark.csr -keystore IWAServerKeyStore.jks
4. Send the CSR to the CA to be signed. The CA signs the certificate and sends back the signed certificate along with the Root and Intermediate certificates.
whaleshark.crt
intermediate.cer
AquariumRoot.cer
5. Import the signed server certificate.
keytool -importcert -file whaleshark.cer -keystore IWAServerKeyStore.jks -alias whaleshark.aquarium.com -trustcacerts
6. View the contents of the KeyStore
keytool -list -keystore IWAServerKeyStore.jks
Keystore type: jks
Keystore provider: SUN
Your keystore contains 3 entries
intermediate.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:65:AC:DC:A4:D8:C3:8A:54:23:72:59:3D:C6:41:D5:79:1D:CB:A9
whaleshark.aquarium.com, Jul 14, 2021, PrivateKeyEntry,
Certificate fingerprint (SHA1): CD:AE:BC:D2:7A:4D:37:A9:3D:24:29:45:1A:72:B3:45:2C:67:3A:56
root.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:FA:EC:28:A6:23:D1:AC:49:24:D4:A3:36:AF:2C:28:4C:AC:79:B4
7. Export the Public Key of the server certificate into a file from the KeyStore
keytool -exportcert -alias whaleshark.aquarium.com -file whaleshark.pub.cer -keystore IWAServerKeyStore.jks -storetype jks
8. Delete the current Public Key from the TrustStore for the MDM
keytool -delete -noprompt -alias whaleshark.pub -keystore IWAServerTrustStore.jks
9. Import the Public Key of the server certificate
keytool -importcert -file whaleshark.pub.cer -keystore IWAServerTrustStore.jks -alias whaleshark.pub -trustcacerts
10. View the contents of the TrustStore
keytool -list -keystore IWAServerTrustStore.jks
Enter keystore password: <Enter the Password used when the KeyStore was created>
Keystore type: jks
Keystore provider: SUN
Your keystore contains 4 entries
Enter keystore password:
Keystore type: jks
Keystore provider: SUN
Your keystore contains 4 entries
whaleshark.pub, Jul 14, 2021, trustedCertEntry,
Certificate fingerprint (SHA1): CD:AE:BC:D2:7A:4D:37:A9:3D:24:29:45:1A:72:B3:45:2C:67:3A:56
intermediate.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:65:AC:DC:A4:D8:C3:8A:54:23:72:59:3D:C6:41:D5:79:1D:CB:A9
root.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:FA:EC:28:A6:23:D1:AC:49:24:D4:A3:36:AF:2C:28:4C:AC:79:B4
mykey, Dec 5, 2019, PrivateKeyEntry,
Certificate fingerprint (SHA1): EF:49:AB:47:AC:A3:49:4A:C4:0C:51:78:23:58:87:22:3A:BC:A4:B5
11. To view the expiration dates of a certificate, run the following command
keytool -list -v -keystore IWAServerTrustStore.jks | more
12. Go to the directory where the DWC KeyStore and TrustStores are located
cd /opt/IBM/IWA/DWC/usr/servers/dwcServer/resources/security
13. Copy the updated KeyStore and TrustStore from the MDM
cp /opt/IBM/IWA/IWS/usr/servers/engineServer/resources/security/IWAServer* .
ls -l
-rw-r--r--. 1 iwadmin iwadmin 5507 Nov 12 20:02 IWAServerKeyStore.jks
-rw-r--r--. 1 iwadmin iwadmin 6465 Nov 12 21:07 IWAServerTrustStore.jks
-rw-------. 1 iwadmin iwadmin 897 Jul 15 17:20 ltpa.keys
-rw-r--r--. 1 iwadmin iwadmin 4503 Nov 12 21:48 TWSServerKeyFile.jks
-rw-r--r--. 1 iwadmin iwadmin 118579 Nov 12 21:48 TWSServerTrustFile.jks
14. Follow the steps in section 4.24.2.6 Verify that DWC is using the new Certificate
15. If the certificate doesn’t show the new expiration date, restart the DWC WLP as shown below. cd /opt/IBM/IWA/DWC/appservertools
./stopAppServer.sh
./startAppServer.sh
3 Renewing the Expired Certificate of the DA
The CA signed certificates start expiring from Nov 20, 2020. As such, these certificates must be renewed ahead of time in order to keep the various components communicating with each other and not interrupt the execution of the workload automation.
Follow the steps below to renew the Certificates for the MDM and DWC.
3. Login as iwadmin on the agent and set the PATH variable to include the key management tool, gsk8capicmd, provided by IWA
export PATH=/opt/IBM/IWA/TWS/tmpGSKit64/8/bin:$PATH
4. Source the script to set the environment as shown below.
. /opt/IBM/IWA/opt/tws_env.sh
5. Backup the existing TWSClientKeyStores
cd /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert
cp TWSClientKeyStore.kdb TWSClientKeyStore.kdb.orig
cp TWSClientKeyStoreJKS.jks TWSClientKeyStoreJKS.jks.orig
6. Generate a CSR from the CMS TWSClientKeyStore.kdb
gsk8capicmd_64 -certreq -create -sigalg SHA256withRSA -size 2048 -db TWSClientKeyStore.kdb -label agent -dn "CN=agent.aquarium.com,OU=BatchOps,O=Aquarium,L=MarianaTrench,ST=PacificOcean,C=US" -file agent.csr -stashed
7. Send the CSR, agent.csr, to the CA to be signed and returned.
8. Once the CA signed certificate is received, copy it to where the agent KeyStore is located, /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert, and import it into the CMS TWSClientKeyStore.kdb
gsk8capicmd_64 -cert -receive -db TWSClientKeyStore.kdb -file agent.cer -default_cert yes -stashed
9. Extract the public certificate for the agent and copy it to the MDM
gsk8capicmd_64 -cert -extract -db TWSClientKeyStore.kdb -label agent -target agent.pub.crt -stashed
cp agent.pub.crt /opt/IBM/IWA/IWS/usr/servers/engineServer/resources/security
10. Delete the Public key of the server’s certificate from the KeyStore
gsk8capicmd_64 -cert -delete -db TWSClientKeyStore.kdb -label whaleshark.pub -stashed
11. Copy the new Public key of the server’s certificate and import it into the KeyStore
cp /opt/IBM/IWA/IWS/usr/servers/engineServer/resources/security/whaleshark.pub.cer
gsk8capicmd_64 -cert -add -db TWSClientKeyStore.kdb -file whaleshark.pub.cer -label whaleshark.pub -trust enable -stashed
12. View the contents of the KeyStore
gsk8capicmd_64 -cert -list -db TWSClientKeyStore.kdb -stashed
Source database passwordCertificates found
Certificates found
* default, - personal, ! trusted, # secret key
! root.cert
! intermediate.cert
! whaleshark.pub
- agent
13. To view the expiration dates of a certificate, run the following command with the label of the certificate
gsk8capicmd_64 -cert -details -label Whaleshark.pub -db TWSClientKeyStore.kdb -stashed | more
14. Delete the expired public certificate of the DA and import the new public certificate into the Primary MDM server’s TrustStore
cd /opt/IBM/IWA/IWS/usr/servers/engineServer/resources/security
keytool -delete -noprompt -alias agent.pub -keystore IWAServerTrustStore.jks
keytool -importcert -file agent.pub.crt -keystore IWAServerTrustStore.jks -alias agent.pub -trustcacerts
15. View the Certificates in the Server TrustStore
keytool -list -keystore IWAServerTrustStore.jks
Enter Keystore Password:
Keystore type: jks
Keystore provider: SUN
Your keystore contains 5 entries
whaleshark.pub, Jul 14, 2021, trustedCertEntry,
Certificate fingerprint (SHA1): CD:AE:BC:D2:7A:4D:37:A9:3D:24:29:45:1A:72:B3:45:2C:67:3A:56
intermediate.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:65:AC:DC:A4:D8:C3:8A:54:23:72:59:3D:C6:41:D5:79:1D:CB:A9
root.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:FA:EC:28:A6:23:D1:AC:49:24:D4:A3:36:AF:2C:28:4C:AC:79:B4
mykey, Dec 5, 2019, PrivateKeyEntry,
Certificate fingerprint (SHA1): EF:49:AB:47:AC:A3:49:4A:C4:0C:51:78:23:58:87:22:3A:BC:A4:B5
agent.pub, Jul 14, 2021, trustedCertEntry,
Certificate fingerprint (SHA1): 43:A8:C3:34:D3:EA:38:4B:D2:F7:38:40:3A:F4:CA:3A:51:7A:C3:F1
16. To view the expiration dates of a certificate, run the following command
keytool -list -v -keystore IWAServerTrustStore.jks | more
17. Restart the MDM
cd /opt/IBM/IWA/IWS/appservertools
./stopAppServer.sh
./startAppServer.sh
18. Follow the steps in the following sections
4.24.3.3 Convert the CMS TWSClientKeyStore to JKS TWSClientKeyStore
4.24.3.5 Restart Agent and Verify
19. Copy the following files to all DAs to update their KeyStores
TWSClientKeyStore.kdb
TWSClientKeyStore.sth
TWSClientKeyStoreJKS.jks
TWSClientKeyStoreJKS.sth
20. For each DA, follow the steps in section 4.24.3.5 Restart Agent and Verify
The new feature, Automatic deployment of security certificates on agents, introduced in version 9.5 Fix Pack 04 applies to Dynamic Agents and simplifies the above process by eliminating steps 4-10. Steps 1-3 must still be completed, and the certificates must be placed in the certificate depot location, <TWSDATA>/TWS/ssl/depot. This dir only exists if a fresh installation was performed using FP4 image. If an existing installation was upgraded to FP4, this directory needs to be created. The certificates are downloaded to an agent in the following scenarios:
- Automatically during fresh installation using twsinst command with the options, --wauser and –wapassword
- Automatically when the certificates are about to expire within 15 days
- Manually by running the command, AgentCertificateDownloader
The following sections describe how to replace the default certificates used by the DA.
1.3.1 Generate a CSR for the DA in the CMS TWSClientKeyStore
Follow the steps below to generate and update the CMS TWSClientKeyStore.kdb
- Login as iwadmin on the agent and set the PATH variable to include the key management tool, gsk8capicmd, provided by IWA
2. Source the script to set the environment as shown below.
. /opt/IBM/IWA/TWS/tws_env.sh
3. Backup the existing TWSClientKeyStores
cd /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert
cp TWSClientKeyStore.kdb TWSClientKeyStore.kdb.orig
cp TWSClientKeyStoreJKS.jks TWSClientKeyStoreJKS.jks.orig
4. Generate a CSR from the CMS TWSClientKeyStore.kdb
gsk8capicmd_64 -certreq -create -sigalg SHA256withRSA -size 2048 -db TWSClientKeyStore.kdb -label agent -dn "CN=agent.aquarium.com,OU=BatchOps,O=Aquarium,L=MarianaTrench,ST=PacificOcean,C=US" -file agent.csr -stashed
5. Send the CSR, agent.csr, to the CA to be signed and returned.
6. Once the CA signed certificate is received, import it into the CMS TWSClientKeyStore.kdb along with the root, intermediate, and MDM server’s public certificate in the order shown below
a. gsk8capicmd_64 -cert -add -db TWSClientKeyStore.kdb -file /home/iwadmin/certs/AquariumRoot.cer -label root.cert -trust enable -stashed
b. gsk8capicmd_64 -cert -add -db TWSClientKeyStore.kdb -file /home/iwadmin/certs/intermediate.cer -label intermediate.cert -trust enable -stashed
c. gsk8capicmd_64 -cert -add -db TWSClientKeyStore.kdb -file /home/iwadmin/certs/whaleshark.pub.cer -label whaleshark.pub -trust enable -stashed
d. gsk8capicmd_64 -cert -receive -db TWSClientKeyStore.kdb -file /opt/IBM/IWA/TWSDATA/ITA/cpa/ita/cert/agent.cer -default_cert yes -stashed
7. Delete the following default certificates
a. gsk8capicmd_64 -cert -delete -db TWSClientKeyStore.kdb -label client
b. gsk8capicmd_64 -cert -delete -db TWSClientKeyStore.kdb -label server
c. gsk8capicmd_64 -cert -delete -db TWSClientKeyStore.kdb -label serverold
8. Extract the public certificate for the agent and copy it to the MDM
gsk8capicmd_64 -cert -extract -db TWSClientKeyStore.kdb -stashed -label agent -target agent.pub.crt
cp agent.pub.crt /home/iwadmin/certs
9. View the contents of the KeyStore
gsk8capicmd_64 -cert -list -db TWSClientKeyStore.kdb
Source database passwordCertificates found
Certificates found
* default, - personal, ! trusted, # secret key
! root.cert
! intermediate.cert
! whaleshark.pub
- agent
1.3.2 Import the public certificate of the DA into the MDM TrustStore
Follow the steps below to Import the public certificate of the DA into the JKS IWAServerTrustStore.jks.
- Login as iwadmin to the MDM and go to the directory where the TrustStore is located
cd /opt/IBM/IWA/IWS/usr/servers/engineServer/resources/security
cp IWAServerTrustStore.jks IWAServerTrustStore.jks.orig
2. Import the public certificate of the DA into the Primary MDM server’s TrustStore
keytool -importcert -file /home/iwadmin/certs/agent.pub.crt -keystore /opt/IBM/IWA/IWS/usr/servers/engineServer/resources/security/IWAServerTrustStore.jks -alias agent.pub -trustcacerts
3. View the Certificates in the Server TrustStore
keytool -list -keystore /opt/IBM/IWA/IWS/usr/servers/engineServer/resources/security/IWAServerTrustStore.jks -storepass iwa4aquarium
Enter Keystore Password:
Keystore type: jks
Keystore provider: SUN
Your keystore contains 5 entries
whaleshark.pub, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): CD:AE:BC:D2:7A:4D:37:A9:3D:24:29:45:1A:72:B3:45:2C:67:3A:56
intermediate.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:65:AC:DC:A4:D8:C3:8A:54:23:72:59:3D:C6:41:D5:79:1D:CB:A9
root.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:FA:EC:28:A6:23:D1:AC:49:24:D4:A3:36:AF:2C:28:4C:AC:79:B4
mykey, Dec 5, 2019, PrivateKeyEntry,
Certificate fingerprint (SHA1): EF:49:AB:47:AC:A3:49:4A:C4:0C:51:78:23:58:87:22:3A:BC:A4:B5
agent.pub, Dec 11, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 43:A8:C3:34:D3:EA:38:4B:D2:F7:38:40:3A:F4:CA:3A:51:7A:C3:F1
4. Restart the Primary MDM
cd /opt/IBM/IWA/IWS/appservertools
./stopAppServer.sh
./startAppServer.sh
1.3.3 Convert the CMS TWSClientKeyStore to JKS TWSClientKeyStore
Follow the steps below to convert the CMS TWSClientKeyStore to JKS TWSClientKeyStore.jks.
- Login as iwadmin to the Primary MDM and go to the directory where the KeyStore is located
cp TWSClientKeyStoreJKS.jks TWSClientKeyStoreJKS.jks.orig
2. Delete any certificates with the extension, arm rm *.arm
3. Run the following command to convert the CMS TWSClientKeyStore to JKS format
/opt/IBM/IWA/IWS/TWS/_uninstall/ACTIONTOOLS/twsManageKey.sh --certPath /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert --jreBinPath /opt/IBM/IWA/IWS/TWS/JavaExt/jre/bin --gsKitDir /opt/IBM/IWA/IWS/TWS/tmpGSKit64/8 --envCmd /opt/IBM/IWA/IWS/TWS/tws_env.sh --itaIni /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/ita.ini
IBM Workload Scheduler Environment Successfully Set !!!
twsManageKey() executing: /opt/IBM/IWA/IWS/TWS/tmpGSKit64/8/bin/gsk8capicmd_64 -cert -extract -db /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStore.kdb -stashed -type cms -format ascii -target /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/ca_root.cert.arm -label root.cert
Certificate was added to keystore
twsManageKey() executing: /opt/IBM/IWA/IWS/TWS/JavaExt/jre/bin/keytool -importcert -keystore /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStoreP12.p12 -storepass default -storetype pkcs12 -file /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/ca_root.cert.arm -alias root.cert -noprompt
twsManageKey() executing: /opt/IBM/IWA/IWS/TWS/tmpGSKit64/8/bin/gsk8capicmd_64 -cert -extract -db /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStore.kdb -stashed -type cms -format ascii -target /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/ca_intermediate.cert.arm -label intermediate.cert
Certificate was added to keystore
twsManageKey() executing: /opt/IBM/IWA/IWS/TWS/JavaExt/jre/bin/keytool -importcert -keystore /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStoreP12.p12 -storepass default -storetype pkcs12 -file /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/ca_intermediate.cert.arm -alias intermediate.cert -noprompt
twsManageKey() executing: /opt/IBM/IWA/IWS/TWS/tmpGSKit64/8/bin/gsk8capicmd_64 -cert -extract -db /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStore.kdb -stashed -type cms -format ascii -target /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/ca_whaleshark.pub.arm -label whaleshark.pub
Certificate was added to keystore
twsManageKey() executing: /opt/IBM/IWA/IWS/TWS/JavaExt/jre/bin/keytool -importcert -keystore /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStoreP12.p12 -storepass default -storetype pkcs12 -file /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/ca_whaleshark.pub.arm -alias whaleshark.pub -noprompt
Importing keystore /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStoreP12.p12 to /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStoreJKS.jks...
Entry for alias agent successfully imported.
Entry for alias root.cert successfully imported.
Entry for alias intermediate.cert successfully imported.
Entry for alias whaleshark.pub successfully imported.
Import command completed: 4 entries successfully imported, 0 entries failed or cancelled
4. View the contents of the JKS ClientKeyStoreJKS. It should be identical to the CMS TWSClientKeyStore
keytool -list -keystore TWSClientKeyStoreJKS.jks -storepass default
Keystore type: jks
Keystore provider: SUN
Your keystore contains 4 entries
whaleshark.pub, Dec 11, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): CD:AE:BC:D2:7A:4D:37:A9:3D:24:29:45:1A:72:B3:45:2C:67:3A:56
intermediate.cert, Dec 11, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:65:AC:DC:A4:D8:C3:8A:54:23:72:59:3D:C6:41:D5:79:1D:CB:A9
agent, Dec 11, 2019, PrivateKeyEntry,
Certificate fingerprint (SHA1): 43:A8:C3:34:D3:EA:38:4B:D2:F7:38:40:3A:F4:CA:3A:51:7A:C3:F1
root.cert, Dec 11, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:FA:EC:28:A6:23:D1:AC:49:24:D4:A3:36:AF:2C:28:4C:AC:79:B4
1.3.4 Update the certificate related parameters in ita.ini of the DA
Follow the steps below to update the certificate related parameters in ita.ini of the DA.
- Login as iwadmin to the Primary MDM and go to the directory where ita.ini is located
2. Open ita.ini file, scroll down to the ITA SSL section and update and verify the following parameters shown in bold.
vi ita.ini
[ITA SSL]
gskit_dir = /usr/Tivoli/TWS/GSKit64/8/lib64
fips_enable = yes
password_file =
cert_label = agent
key_db_name = TWSClientKeyStore
key_repository_dir = /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert
gskit_libs_installed = 1
conn_verify = 1
ca_cert_fname = /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/cacert.pem
java_truststore_password_file = /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStoreJKS.sth
java_truststore_file = /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStoreJKS.jks
3. Save and exit.
1.3.5 Restart Agent and Verify
Follow the steps below to restart the agent and verify its connectivity to the MDM server.
- Go to the agent’s home directory
./ShutDownLwa
./StartUpLwa
2. Login to the DWC and navigate to Monitor Workload, Workstation and make sure that it is linked and running.
3. If it not linked and running, check the agent’s logfile
cd /opt/IBM/IWA/TWSDATA/stdlist/JM/
tail JobManager_message.log
2019-11-13 15:43:10.351-05:00|2046801664|3225|<server_name>.aquarium.com|AWSITA081E The agent can not send the resource information to "https://<server_name>.aquarium.com:31116/JobManagerRESTWeb/JobScheduler/resource". The error is: "AWSITA245E An error occurred getting the response of the HTTP request. The error is "CURL error 35".".
4. Review the steps above and verify that each of the step is executed successfully.
5. If the agent is able to connect successfully to the MDM, the last message in the logfile indicates that it is able to send information to the MDM server.
2019-11-13 19:18:26.461-05:00|INFO|JobManager|18446744071629174528|30204|whaleshark.aquarium.com|AWSITA083I Resource information was sent to "https://whaleshark.aquarium.com:31116/JobManagerRESTWeb/JobScheduler/resource".
6. To verify two-way communication between the DA and MDM, submit a test job as follows:
a. Login as iwadmin to the MDM
b. Run conman in interactive mode conman
c. Create and submit a job on the fly sbd whaleshark_da#”echo Hello”;logon=iwadmin
d. Keep running the following command until the job completes successfully. sj whaleshark_da#JOBS.ECHO
e. If the job stays stuck in WAIT state, look at the joblog for any errors by running the following command. sj whaleshark_da#JOBS.ECHO;stdlist
f. Review the steps above and verify that each of the step is executed successfully.
g. Type e followed by an enter to exit conman.
7. Follow the steps in section 4.6 to replicate the TWS Client KeyStores on all DAs to enable SSL communication between MDM and DAs using CA signed certificates
1.4 Update the SSL settings of a DA
Follow the steps below to update the SSL settings of a Dynamic Agent
1.Logon to the server as iwadmin (Unix) or Aquarium\iwadmin (Windows) user
2.Copy the Cliet KeyStore files from the MDM server to the DA
Unix
cd /opt/IBM/IWA/TWSDATA/ITA/cpa/ita/cert
mkdir backup
cp TWSClient* backup
Run the following command with whaleshark (for Dev) or tws (for Prod)
scp iwadmin@whaleshark:/opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert/TWSClientKeyStore* .
The authenticity of host 'whaleshark.aquarium.com (10.150.35.59)' can't be established.
ECDSA key fingerprint is SHA256:Xwo1hl+qLUsLx5EPpSvatBQVNbn89frtabLOao5QpWQ.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'whaleshark.aquarium.com,10.150.35.59' (ECDSA) to the list of known hosts.
iwadmin@whaleshark.aquarium.com's password: <enter password for iwadmin>
TWSClientKeyStore.kdb 100% 20KB 12.0MB/s 00:00
TWSClientKeyStore.sth 100% 129 182.5KB/s 00:00
TWSClientKeyStoreJKS.jks 100% 11KB 5.2MB/s 00:00
TWSClientKeyStoreJKS.sth 100% 129 98.6KB/s 00:00
Windows
cd \IBM\IWA\TWS\ITA\cpa\ita\cert
mkdir backup
copy TWSClient* backup
Launch Winscp and connect to whaleshark (for Dev) or tws (for Prod) as iwadmin
Copy the following files from the whaleshark or tws to the DA
From Dir: /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert
To Dir: \IBM\IWA\TWS\ITA\cpa\ita\cert
Files: TWSClientKeyStore.kdb
TWSClientKeyStore.sth
TWSClientKeyStoreJKS.jks
TWSClientKeyStoreJKS.sth
3. Go to the following directory and edit ita.ini
Unix
cd /opt/IBM/IWA/TWSDATA/ITA/cpa/ita
vi ita.ini
Windows
cd \IBM\IWA\TWS\ITA\cpa\ita
notepad ita.ini
4.Make the following changes
ssl_port=32114
cert_label=agent
Add the following new settings
sslv3_cipher = NONE
tls10_cipher = NONE
tls11_cipher = NONE
tls12_cipher = DFLT
1.5 Enable a DA
When an FTA was installed, the DA was also installed, but not enabled. Follow the steps below to enable the DA.
1.Logon to the server as iwadmin (Unix) or Aquarium\iwadmin (Windows) user
2. Go to the following directory and edit JobManager.ini
Unix
cd /opt/IBM/IWA/TWSDATA/ITA/cpa/config
vi JobManager.ini
Windows
cd \IBM\IWA\TWS\ITA\cpa\config
notepad JobManager.ini
3.Make the following changes in bold
ThisWorkstation = <short_hostnem>_DA
FullyQualifiedHostname = <short_hostnem>.aquarium.com
ResourceAdvisorUrl = https://whaleshark.aquarium.com:32116/JobManagerRESTWeb/JobScheduler/resource (for Dev)
https://iwa.aquarium.com:32116/JobManagerRESTWeb/JobScheduler/resource (for Prod)
ComputerSystemDisplayName = <short_hostnem>_DA
4.Start the DA
Unix
cd /opt/IBM/IWA/TWS
./StartUpLwa
Windows
cd \IBM\IWA\TWS
StartUpLwa
5.Verify that the DA is registered with the server. If it doesn’t show, give it a few minutes and run the following command again.
Login as iwadmin on whaleshark (for Dev) or tws (for Prod)
conman sc <short_hostnem>_DA
1.6 Prepare the MDM for SSL between MDM <> FTA
Follow the steps below to enable SSL between MDM and FTA communication.
1.If communication between the MDM and FTA also needs to be ecncrypted with custom certificates, then the following certificates need to be acquired:
TWSClient.key A private key of the certificate for the FTA, in PEM format
TWSClient.cer The CA signed certificate for the FTA, in PEM format
password.sth The password to access the private key, TWSClient.key, in
base64
TWSTrustCertificates.cer The certificates of all CAs that the FTA needs to trust
(i.e. both the Root and Intermediate CA), in PEM format
2.Place the above custom certificates in the following dir on the MDM. Note that the IBM self-signed certificates are already provided in the same dir. Replace them with the custom certificates.
/opt/IBM/IWA/IWS/TWS/ssl/OpenSSL
3.Logon to the MDM server, whaleshark, as iwadmin user
4. Go to the following directory and edit localopts
cd /opt/IBM/IWA/TWSDATA
vi localopts
5.Make the following changes in bold
nm SSL port =32113
SSL key ="/opt/IBM/IWA/IWS/TWS/ssl/OpenSSL/TWSClient.key"
SSL certificate ="/opt/IBM/IWA/IWS/TWS/ssl/OpenSSL/TWSClient.cer"
SSL key pwd ="/opt/IBM/IWA/IWS/TWS/ssl/OpenSSL/password.sth"
SSL CA certificate ="/opt/IBM/IWA/IWS/TWS/ssl/OpenSSL/TWSTrustCertificates.cer"
SSL random seed ="/opt/IBM/IWA/IWS/TWS/ssl/OpenSSL/TWS.rnd"
SSL Encryption Cipher =TLSv1.2
CLI SSL cipher=TLSv1.2
6.Update the Workstation definition of the MDM with the following settings in bold.
CPUNAME WHALESHARK
DESCRIPTION "This workstation is the Master Domain Manager (MDM)"
OS UNIX
NODE whaleshark.aquarium.com TCPADDR 32111
SECUREADDR 32113
TIMEZONE America/Bogota
DOMAIN MASTERDM
FOR MAESTRO
TYPE MANAGER
AUTOLINK ON
BEHINDFIREWALL OFF
SECURITYLEVEL ENABLED
FULLSTATUS ON
END
7.Update the Workstation definition of each FTA with the following settings in bold. For example, the definition of the FTA, GLOWFISH, is shownn below. Do not modify the definitions of the MASTERAGENTS, WHALESHARK_DWB, and WHALESHARK_DA
composer cr all.workstations.txt from ws=@
CPUNAME GLOWFISH
OS WNT
NODE glowfish.aquarium.com TCPADDR 32111
SECUREADDR 32113
TIMEZONE America/Bogota
DOMAIN MASTERDM
FOR MAESTRO
TYPE FTA
AUTOLINK ON
BEHINDFIREWALL OFF
SECURITYLEVEL ON
FULLSTATUS OFF
END
8.Reimport all modified FTA definitions
composer replace all.workstations.txt
9.Update the plan so that all updated FTA definitions are reflected in the plan.
optman chg cf = all
JnextPlan -for 0000
optman chg cf = yes
10.Stop the MDM
conman “stop;wait”
conman “shut;wait”
11.Start the MDM
cd /opt/IBM/IWA/IWS/TWS
./StartUp
conman start
12. Verify that optman and composer can run successfully.
optman ls
composer li vt=main_table
1.7 Update the SSL settings of an FTA
Follow the steps below to update the SSL settings in localopts of the Fault-Tolerant Agent (FTA).
1.If communication between the MDM and FTA also needs to be ecncrypted with custom certificates, then the following certificates need to be acquired:
TWSClient.key A private key of the certificate for the FTA, in PEM format
TWSClient.cer The CA signed certificate for the FTA, in PEM format
password.sth The password to access the private key, TWSClient.key, in
base64
TWSTrustCertificates.cer The certificates of all CAs that the FTA needs to trust
(i.e. both the Root and Intermediate CA), in PEM format
2.Place the above custom certificates in the following dir on the FTA. Note that the IBM self-signed certificates are already provided in the same dir. Replace them with the custom certificates.
/opt/IBM/IWA/IWS/TWS/ssl/OpenSSL
3.Logon to the server as iwadmin (Unix) or Aquarium\iwadmin (Windows) user
4. Go to the following directory and edit localopts
Unix
cd /opt/IBM/IWA/TWSDATA
vi localopts
Windows
cd \IBM\IWA\TWS
notepad localopts
5. Make the following changes in bold
Both
nm SSL port =32113
Unix
SSL key ="/opt/IBM/IWA/TWS/ssl/OpenSSL/TWSClient.key"
SSL certificate ="/opt/IBM/IWA/TWS/ssl/OpenSSL/TWSClient.cer"
SSL key pwd ="/opt/IBM/IWA/TWS/ssl/OpenSSL/password.sth"
SSL CA certificate ="/opt/IBM/IWA/TWS/ssl/OpenSSL/TWSTrustCertificates.cer"
SSL random seed ="/opt/IBM/IWA/TWS/ssl/OpenSSL/TWS.rnd"
Windows
SSL key ="C:\IBM\IWA\TWS\ssl\OpenSSL\TWSClient.key"
SSL certificate ="C:\IBM\IWA\TWS\ssl\OpenSSL\TWSClient.cer"
SSL key pwd ="C:\IBM\IWA\TWS\ssl\OpenSSL\password.sth"
SSL CA certificate ="C:\IBM\IWA\TWS\ssl\OpenSSL\TWSTrustCertificates.cer"
SSL random seed ="C:\IBM\IWA\TWS\ssl\OpenSSL\TWS.rnd"
Both
SSL Encryption Cipher =TLSv1.2
CLI SSL cipher=TLSv1.2
6. Stop the FTA
conman “stop;wait”
conman “shut;wait”
7. Start the FTA
Unix
cd /opt/IBM/IWA/TWS
./StartUp
conman link [whaleshark for Dev or tws for Prod]
conman start
Windows
cd \IBM\IWA\TWS
StartUp
conman link [whaleshark for Dev or tws for Prod]
conman start
8. Verify that composer can be run successfully. composer li vt=main_table
9.Verify that the FTA linked with the server successfully and it shows all the flags, LTI JW, as shown below as an example for GLOWFISH
Login as iwadmin on whaleshark (for Dev) or tws (for Prod)
conman sc <short_hostnem>
GLOWFISH 12 WIN FTA 10 0 03/18/20 23:59 LTI JW MASTERDM
2 Renewing the Expired Certificate of the MDM & DWC
The CA signed certificates start expiring from Nov 20, 2020. As such, these certificates must be renewed ahead of time in order to keep the various components communicating with each other and not interrupt the execution of the workload automation.
Follow the steps below to renew the Certificates for the MDM and DWC.
- If the original CSR created in section 4.24.2.2 Generate a CSR for MDM is still available, send it to the CA and have it signed. If it is not available, generate a new CSR following the steps below.
- Go to the dir where the current KeyStore is located.
3. Generate a Certificate Signing Request CSR for the MDM server.
keytool -certreq -sigalg SHA256withRSA -alias whaleshark.aquarium.com -file whaleshark.csr -keystore IWAServerKeyStore.jks
4. Send the CSR to the CA to be signed. The CA signs the certificate and sends back the signed certificate along with the Root and Intermediate certificates.
whaleshark.crt
intermediate.cer
AquariumRoot.cer
5. Import the signed server certificate.
keytool -importcert -file whaleshark.cer -keystore IWAServerKeyStore.jks -alias whaleshark.aquarium.com -trustcacerts
6. View the contents of the KeyStore
keytool -list -keystore IWAServerKeyStore.jks
Keystore type: jks
Keystore provider: SUN
Your keystore contains 3 entries
intermediate.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:65:AC:DC:A4:D8:C3:8A:54:23:72:59:3D:C6:41:D5:79:1D:CB:A9
whaleshark.aquarium.com, Jul 14, 2021, PrivateKeyEntry,
Certificate fingerprint (SHA1): CD:AE:BC:D2:7A:4D:37:A9:3D:24:29:45:1A:72:B3:45:2C:67:3A:56
root.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:FA:EC:28:A6:23:D1:AC:49:24:D4:A3:36:AF:2C:28:4C:AC:79:B4
7. Export the Public Key of the server certificate into a file from the KeyStore
keytool -exportcert -alias whaleshark.aquarium.com -file whaleshark.pub.cer -keystore IWAServerKeyStore.jks -storetype jks
8. Delete the current Public Key from the TrustStore for the MDM
keytool -delete -noprompt -alias whaleshark.pub -keystore IWAServerTrustStore.jks
9. Import the Public Key of the server certificate
keytool -importcert -file whaleshark.pub.cer -keystore IWAServerTrustStore.jks -alias whaleshark.pub -trustcacerts
10. View the contents of the TrustStore
keytool -list -keystore IWAServerTrustStore.jks
Enter keystore password: <Enter the Password used when the KeyStore was created>
Keystore type: jks
Keystore provider: SUN
Your keystore contains 4 entries
Enter keystore password:
Keystore type: jks
Keystore provider: SUN
Your keystore contains 4 entries
whaleshark.pub, Jul 14, 2021, trustedCertEntry,
Certificate fingerprint (SHA1): CD:AE:BC:D2:7A:4D:37:A9:3D:24:29:45:1A:72:B3:45:2C:67:3A:56
intermediate.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:65:AC:DC:A4:D8:C3:8A:54:23:72:59:3D:C6:41:D5:79:1D:CB:A9
root.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:FA:EC:28:A6:23:D1:AC:49:24:D4:A3:36:AF:2C:28:4C:AC:79:B4
mykey, Dec 5, 2019, PrivateKeyEntry,
Certificate fingerprint (SHA1): EF:49:AB:47:AC:A3:49:4A:C4:0C:51:78:23:58:87:22:3A:BC:A4:B5
11. To view the expiration dates of a certificate, run the following command
keytool -list -v -keystore IWAServerTrustStore.jks | more
12. Go to the directory where the DWC KeyStore and TrustStores are located
cd /opt/IBM/IWA/DWC/usr/servers/dwcServer/resources/security
13. Copy the updated KeyStore and TrustStore from the MDM
cp /opt/IBM/IWA/IWS/usr/servers/engineServer/resources/security/IWAServer* .
ls -l
-rw-r--r--. 1 iwadmin iwadmin 5507 Nov 12 20:02 IWAServerKeyStore.jks
-rw-r--r--. 1 iwadmin iwadmin 6465 Nov 12 21:07 IWAServerTrustStore.jks
-rw-------. 1 iwadmin iwadmin 897 Jul 15 17:20 ltpa.keys
-rw-r--r--. 1 iwadmin iwadmin 4503 Nov 12 21:48 TWSServerKeyFile.jks
-rw-r--r--. 1 iwadmin iwadmin 118579 Nov 12 21:48 TWSServerTrustFile.jks
14. Follow the steps in section 4.24.2.6 Verify that DWC is using the new Certificate
15. If the certificate doesn’t show the new expiration date, restart the DWC WLP as shown below. cd /opt/IBM/IWA/DWC/appservertools
./stopAppServer.sh
./startAppServer.sh
3 Renewing the Expired Certificate of the DA
The CA signed certificates start expiring from Nov 20, 2020. As such, these certificates must be renewed ahead of time in order to keep the various components communicating with each other and not interrupt the execution of the workload automation.
Follow the steps below to renew the Certificates for the MDM and DWC.
- If the original CSR created in section 4.24.3.1 Generate a CSR for the DA in the CMS TWSClientKeyStore is still available, send it to the CA and have it signed. If it is not available, generate a new CSR following the steps.
- Go to the dir where the current KeyStore is located
3. Login as iwadmin on the agent and set the PATH variable to include the key management tool, gsk8capicmd, provided by IWA
export PATH=/opt/IBM/IWA/TWS/tmpGSKit64/8/bin:$PATH
4. Source the script to set the environment as shown below.
. /opt/IBM/IWA/opt/tws_env.sh
5. Backup the existing TWSClientKeyStores
cd /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert
cp TWSClientKeyStore.kdb TWSClientKeyStore.kdb.orig
cp TWSClientKeyStoreJKS.jks TWSClientKeyStoreJKS.jks.orig
6. Generate a CSR from the CMS TWSClientKeyStore.kdb
gsk8capicmd_64 -certreq -create -sigalg SHA256withRSA -size 2048 -db TWSClientKeyStore.kdb -label agent -dn "CN=agent.aquarium.com,OU=BatchOps,O=Aquarium,L=MarianaTrench,ST=PacificOcean,C=US" -file agent.csr -stashed
7. Send the CSR, agent.csr, to the CA to be signed and returned.
8. Once the CA signed certificate is received, copy it to where the agent KeyStore is located, /opt/IBM/IWA/IWS/TWSDATA/ITA/cpa/ita/cert, and import it into the CMS TWSClientKeyStore.kdb
gsk8capicmd_64 -cert -receive -db TWSClientKeyStore.kdb -file agent.cer -default_cert yes -stashed
9. Extract the public certificate for the agent and copy it to the MDM
gsk8capicmd_64 -cert -extract -db TWSClientKeyStore.kdb -label agent -target agent.pub.crt -stashed
cp agent.pub.crt /opt/IBM/IWA/IWS/usr/servers/engineServer/resources/security
10. Delete the Public key of the server’s certificate from the KeyStore
gsk8capicmd_64 -cert -delete -db TWSClientKeyStore.kdb -label whaleshark.pub -stashed
11. Copy the new Public key of the server’s certificate and import it into the KeyStore
cp /opt/IBM/IWA/IWS/usr/servers/engineServer/resources/security/whaleshark.pub.cer
gsk8capicmd_64 -cert -add -db TWSClientKeyStore.kdb -file whaleshark.pub.cer -label whaleshark.pub -trust enable -stashed
12. View the contents of the KeyStore
gsk8capicmd_64 -cert -list -db TWSClientKeyStore.kdb -stashed
Source database passwordCertificates found
Certificates found
* default, - personal, ! trusted, # secret key
! root.cert
! intermediate.cert
! whaleshark.pub
- agent
13. To view the expiration dates of a certificate, run the following command with the label of the certificate
gsk8capicmd_64 -cert -details -label Whaleshark.pub -db TWSClientKeyStore.kdb -stashed | more
14. Delete the expired public certificate of the DA and import the new public certificate into the Primary MDM server’s TrustStore
cd /opt/IBM/IWA/IWS/usr/servers/engineServer/resources/security
keytool -delete -noprompt -alias agent.pub -keystore IWAServerTrustStore.jks
keytool -importcert -file agent.pub.crt -keystore IWAServerTrustStore.jks -alias agent.pub -trustcacerts
15. View the Certificates in the Server TrustStore
keytool -list -keystore IWAServerTrustStore.jks
Enter Keystore Password:
Keystore type: jks
Keystore provider: SUN
Your keystore contains 5 entries
whaleshark.pub, Jul 14, 2021, trustedCertEntry,
Certificate fingerprint (SHA1): CD:AE:BC:D2:7A:4D:37:A9:3D:24:29:45:1A:72:B3:45:2C:67:3A:56
intermediate.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:65:AC:DC:A4:D8:C3:8A:54:23:72:59:3D:C6:41:D5:79:1D:CB:A9
root.cert, Dec 5, 2019, trustedCertEntry,
Certificate fingerprint (SHA1): 33:FA:EC:28:A6:23:D1:AC:49:24:D4:A3:36:AF:2C:28:4C:AC:79:B4
mykey, Dec 5, 2019, PrivateKeyEntry,
Certificate fingerprint (SHA1): EF:49:AB:47:AC:A3:49:4A:C4:0C:51:78:23:58:87:22:3A:BC:A4:B5
agent.pub, Jul 14, 2021, trustedCertEntry,
Certificate fingerprint (SHA1): 43:A8:C3:34:D3:EA:38:4B:D2:F7:38:40:3A:F4:CA:3A:51:7A:C3:F1
16. To view the expiration dates of a certificate, run the following command
keytool -list -v -keystore IWAServerTrustStore.jks | more
17. Restart the MDM
cd /opt/IBM/IWA/IWS/appservertools
./stopAppServer.sh
./startAppServer.sh
18. Follow the steps in the following sections
4.24.3.3 Convert the CMS TWSClientKeyStore to JKS TWSClientKeyStore
4.24.3.5 Restart Agent and Verify
19. Copy the following files to all DAs to update their KeyStores
TWSClientKeyStore.kdb
TWSClientKeyStore.sth
TWSClientKeyStoreJKS.jks
TWSClientKeyStoreJKS.sth
20. For each DA, follow the steps in section 4.24.3.5 Restart Agent and Verify
Author
Sajjad M. Kabir
Solutions Architect
HCL Lab Services
Sajjad Kabir is an Information Technology professional with over 25 years of diverse industry experience with primary emphasis in IT Architecture and Service Management. Extensive experiences in management, architecture, design, development, implementation, and systems integration solutions in multiple industries, platforms, and network environments.